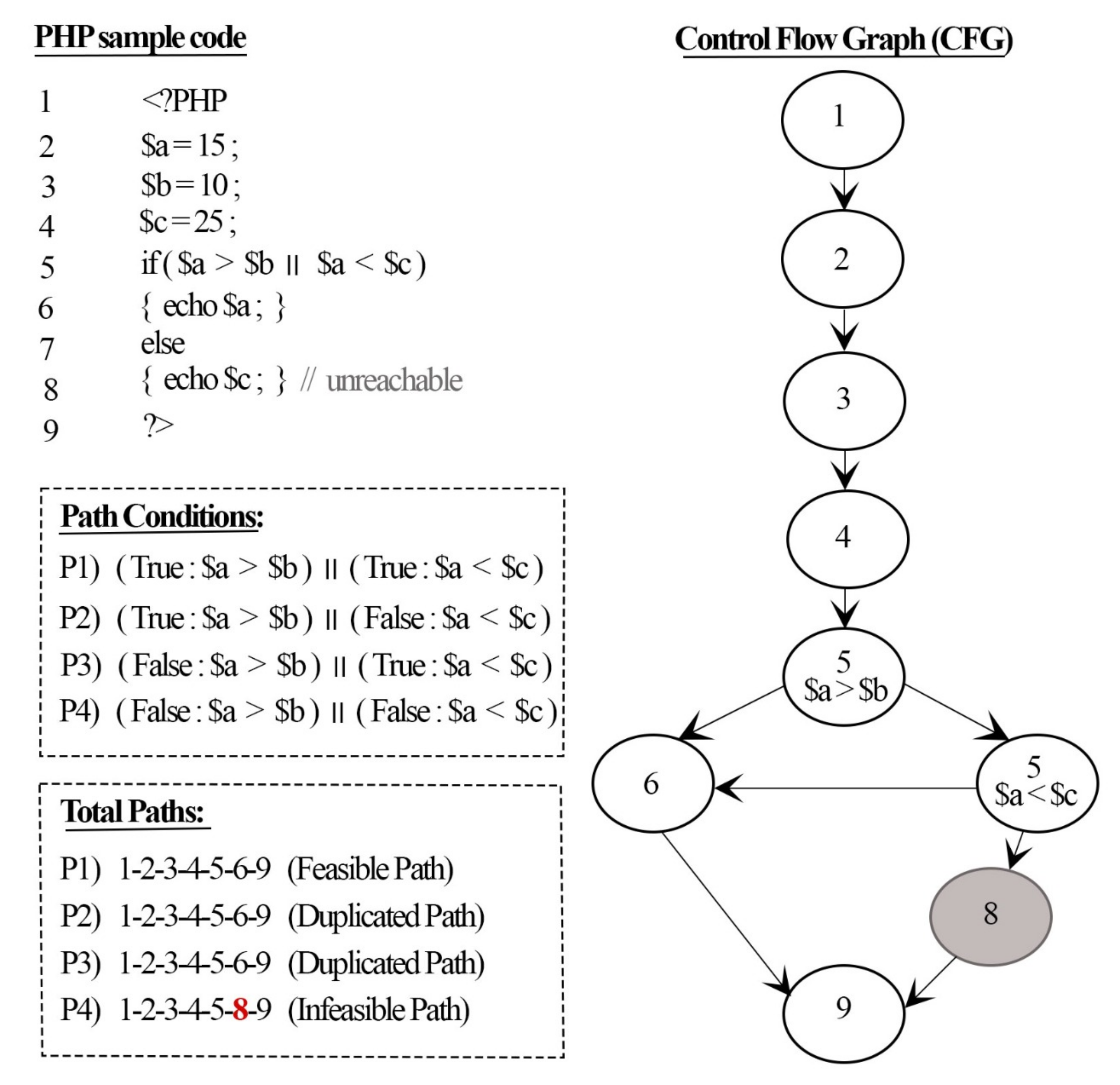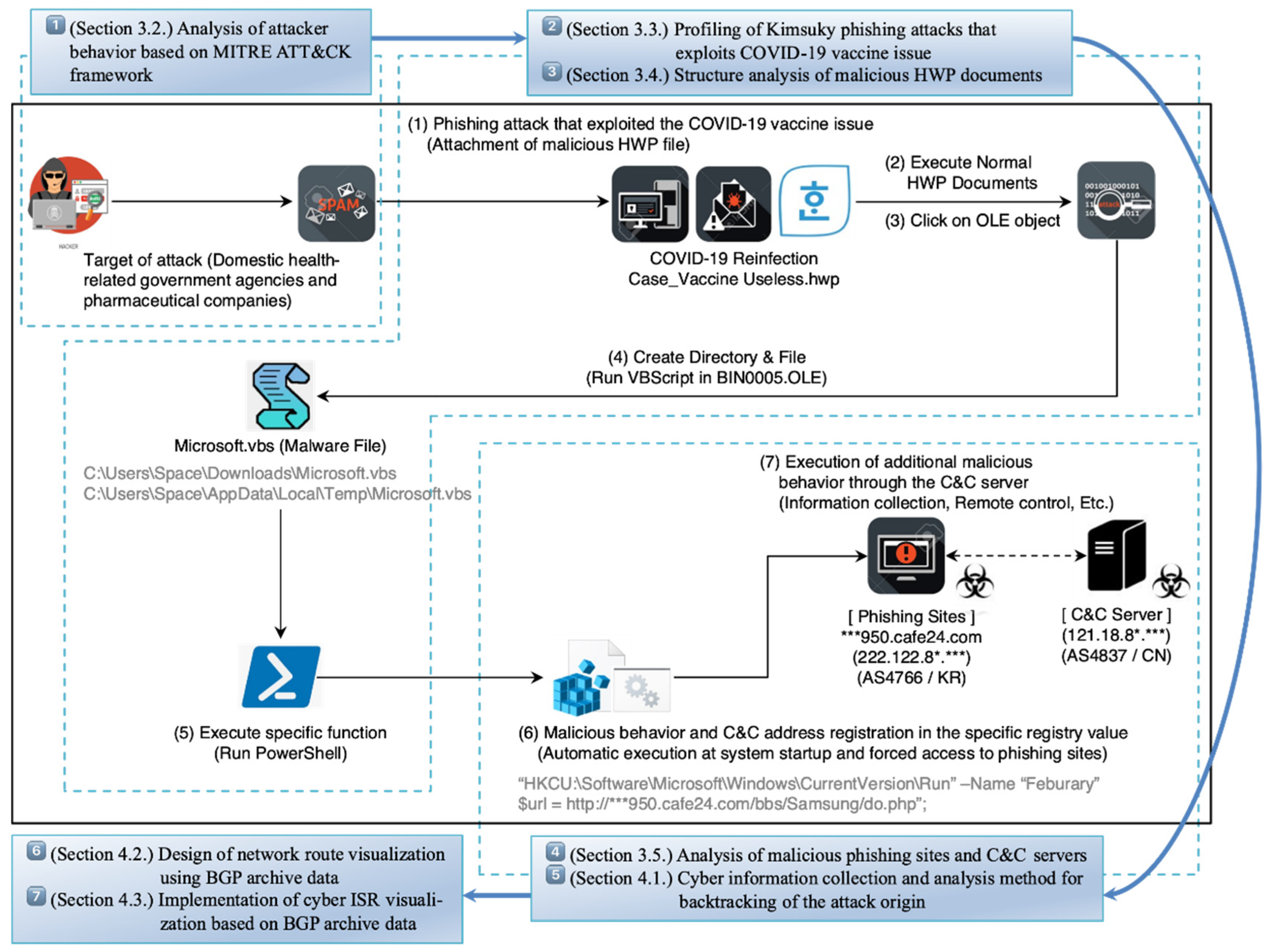
Electronics | Free Full-Text | Research on Cyber ISR Visualization Method Based on BGP Archive Data through Hacking Case Analysis of North Korean Cyber-Attack Groups
Service Vulnerabilities: Shared Hosting Symlink Security Issue Still Widely Exploited on Unpatched Servers